|
Mikko H. Hypponen Fighting Viruses, Defending the Internet delivered July 2011, Edinburgh, Scotland
[AUTHENTICITY CERTIFIED: Text version below transcribed directly from audio]
And itís happening during our lifetimes. Iím pretty sure that when they will be writing history books hundreds of years from now, this time our generation will be remembered as the generation that got online, the generation that built something really and truly global. But, yes, itís also true that the internet has problems, very serious problems, problems with security and problems with privacy. And Iíve spent my career fighting these problems. So, let me show you something. This here is Brain. This is a floppy disk five and a quarter inch floppy disk infected by Brain.A. Itís the first virus we ever found for PC computers.
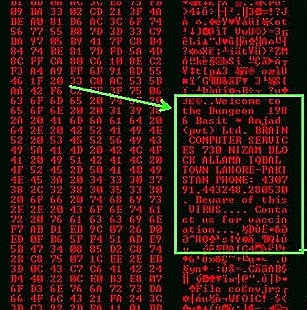
And we actually know where Brain came from. We know because it says so inside the code. Letís take a look. All right, thatís the boot sector of an infected floppy and if we actually take a closer look inside, weíll see that right there it actually says, ďWelcome to the dungeon.Ē And then it continues saying, ď1986 Basit and Amjad.Ē And Basit and Amjad are first names, Pakistani first names. In fact, thereís a phone number and an address to Pakistan.
Now, 1986, now itís 2011, thatís 25 years ago. The PC virus problem is 25 years old now. So, half a year ago, I decided to go to Pakistan myself. So letís see, hereís a couple of photos I took while I was in Pakistan. This is from the city of Lahore which is around 300 km south from Abbottabad where Bin Laden was caught. Hereís a typical street view and hereís the street or road leading to this building which is 730 Nizam block at Allama Iqbal town. And I knocked on the door. You want to guess who opened the door? Basit and Amjad, they are still there. So here standing up is Basit, sitting down is his brother Amjad. These are the guys who wrote the first PC virus. And of course we had a very interesting discussion. I -- I asked them why. I asked them how they feel about what they started. And I got some sort of satisfaction from learning that both Basit and Amjad had had their computers infected dozens of time by completely unrelated other viruses over these years. So there is, thereís some sort of justice in the world after all. Now the viruses that we used to see in the 1980s and 1990s obviously are not a problem any more. So let me just show you a couple of examples what they used to look like. What Iím running here is a system that enables me to run age-old programs on a modern computer. So let me just mount some drives, go over there. And what we have here is a list of old viruses. So let me just run some viruses on my computer. For example, letís go with the Centipede virus first. And you can see at the top of the screen, thereís a centipede scrolling across your computer when you get infected by this one. You know that youíre infected because it actually shows up. Hereís another one. This is the virus called Crash invented in Russia in 1992. Let me show you one which actually makes some sound. (Siren sound.) And the last example, guess what the Walker virus does? Yes, thereís a guy walking across your screen once you get infected. So, it used to be fairly easy to know that youíre infected by a virus when the viruses were written by hobbyists and teenagers. Today, they are no longer being written by hobbyists and teenagers. Today, viruses are a global problem. What we have here in the background is an example of our systems that we run in our labs where we track virus infections worldwide. So we can actually see in real time that weíve just blocked viruses in Sweden and Taiwan and Russia and elsewhere. In fact, if I just connect back to our lab systems through the web, we can see in real time just some kind of idea of how many viruses, how many new examples of malware we find every single day. Hereís the latest virus we found, in a file called Server@exe and we found it right over here 3 seconds ago, the previous one 6 seconds ago. And if we just scroll around, itís a, itís just massive. We find tens of thousands even hundreds of thousands and thatís the last 20 minutes of malware every single day. So where are all these coming from then? Well, today itís the organized criminal gangs writing these viruses, because they make money with their viruses. Itís gangs like, letís go to GangstaBucks.com. This is a website operating in Moscow where these guys are actually buying infected computers. So if you are a virus writer and youíre capable of infecting Windows computers but you donít know what to do with them, you can sell those infected computers, somebody elseís computers to these guys. And theyíll actually pay you money for those computers.
So how do these guys then monetize those infected computers? Well, thereís multiple different ways such as banking trojans which will steal money from your online banking accounts when you do online banking or keyloggers. Keyloggers silently sit on your computer hidden from view and they record everything you type. So youíre sitting on your computer, youíre doing Google searches. Every single Google search you type is saved and sent to the criminals. Every single email you write is saved and sent to the criminals, same thing with every single password and so on. But the thing that they are actually looking for most are sessions where you go online and do online purchases in any online store. Because when you do purchases in online store you will by typing in your name, the delivery address, your credit card number, and the credit card security codes. And thatís, hereís an example of a file we found from a server a couple of weeks ago, thatís the credit card number, thatís the expiration date, thatís a security code, and thatís the name of the owner of the card. And once you gain access to other peoplesí credit card information, you can just go online and buy whatever you want with this information. And that, obviously is a problem. We now have a whole underground marketplace and business ecosystem built around online crime. One example of how these guys actually are capable of monetizing their operations, if you go and have a look at the pages of Interpol and search for wanted persons. We find guys like Bjorn Sundin, originally from Sweden and his partner in crime also listed on the Interpol wanted pages, Mr. Shaileshkumar Jain, a U.S. citizen.
These guys were running a -- an operation called I.M.U., a cybercrime operation through which they netted millions. Theyíre both right now on run. Nobody knows where they are. U.S. officials just couple of weeks ago froze a Swiss bank account belonging to Mr. Jain and that bank account had 14.9 million U.S. dollars on it. So the amount of money online crime generates is significant and that means that the online criminals can actually afford to invest in their attacks. We know that online criminals are hiring programmers, hiring testing people, testing their code, having back-end systems with SQL databases. And they can afford to watch how we work, like how security people work and try to work their way around any security precautions we can build. And they also use the global nature of Internet to their advantage. I mean, Internet is international, thatís why we call it the Internet. And if you just go and take a look at whatís happening in the online world, thereís a video built by Clarified Networks which illustrates how one single malware family is able to move around the world. This operation believed to be originally from Estonia moves around from one country to another as soon as the website is tried to shut down. So you just canít shut these guys down. They will switch from one country to another, from one jurisdiction to another, moving around the world using the fact that we donít have capability to globally police operations like this. So the Internet is as if somebody would have given free plane tickets to all the online criminals of the world. Now the criminals who werenít capable of reaching us before can reach us. So how do you actually go around finding online criminals? How do you actually track them down? Let me give you an example. What we have here is one exploit file. Here Iím looking at the hex dump of a image file which contains an exploit. And that basically means if you try to view this image file on your Windows computer, it actually takes over your computer and runs code. And if you take a closer look at this image file, well thereís the image header, and there the actual code of the attack starts. And that code has been encrypted so letís decrypt it. It has been encrypted with XOR function 97. You just have to believe me, it is, it is. And a, we can go here and actually start decrypting it. Well, the yellow part of the code is now decrypted and I know it doesnít really look much different from the original, but just keep staring at it. Youíll actually see that down here you can see a web address, unionseek.com/d/ioo.exe. And when you view this image on your computer, itís actually going to run, download and run that program and thatís a backdoor which will take over your computer. But even more interestingly, if we continue decrypting, weíll find this mysterious string which says O600KO78RUS. That code is there underneath the encryption as some sort of a signature. Itís not used for anything and I was looking at that and trying to figure out what it means. So obviously I Googled for it. I got zero hits, wasnít there. So I spoke with the guys in the lab and we have a couple of Russian guys in our labs and -- and one of them mentioned, well it ends in RUS like Russia. All right? And 78 is the city code for the city of St. Petersburg. For example, you can find it from some phone numbers and -- and car license plates and stuff like that. So I went looking for contacts in St. Petersburg and through a long road we eventually found this one particular website. Hereís this Russian guy whoís been operating online for a number of years, who runs his own website, and he runs a blog under the popular Live Journal. And on this blog, he blogs about his life, about his life in St. Petersburg, heís in his early twenties, about his cat, about his girl friend, and he drives a very nice car. In fact, this guy drives a Mercedes Benz S600 V12 with a 6 liter engine with more than 400 horsepower. And thatís a nice car for a twenty-something old kid in St. Petersburg. How do I know about this car? Because he blogged about the car. He actually had a car accident in downtown St. Petersburg. He actually crashed his car into another car and he put blogged images about the car accident, thatís his Mercedes, right here is the Lada Samara he crashed into.
So what happens when online criminals are actually caught? Well, in most cases actually never gets this far. The vast majority of the online crime cases, we donít even know which continent the attacks were coming from, and even if we are able to find online criminals quite often there is no outcome. The local police doesnít act or if they do, thereís no, not enough evidence or for some reason we canít take them down. I wish it would be easier. Unfortunately it isnít. And things are also changing at a very rapid pace. Youíve all heard about things like Stuxnet. So if you look at what Stuxnet actually did, is that it infected these, thatís a Siemens S7-400 PLC, programmable logic computer. And this is what runs our infrastructure. This is what runs everything around us. PLCs, these small boxes which have no display, no -- no keyboard, which are programmed, are put in place and they do their job. For example, the elevators in this building most likely are controlled by one of these. And when Stuxnet infects one of these, thatís a massive revolution on the kinds of risks we have to worry about, because everything around us is being run by these. I mean, we have critical infrastructure, you go to any -- any factory, any power plant, any chemical plant, any food processing plant, you look around, everything is being run by computers. Everything is being run by computers. Everything is reliant on these computers working. We have become very reliant on Internet, on basic things like electricity obviously, on computers working. And this really is something which creates completely new problems for us. We must have some way of continuing to work even if computers fail. [turns on overhead projector, uses slide transparency]
So preparedness means that we can do stuff even when the things that we take for granted arenít there. Itís actually very basic stuff. Iím thinking about continuity. Iím thinking about backups, thinking about the things that actually matter. Now, I told you, I love Internet, I do. Think about all the services we have online. Think about if they are taken away from you, if one day you donít actually have them for some reason or other. I see beauty in the future of the Internet but Iím worried that we might not see that. Iím worried that we are running into problems because of online crime. Online crime is the one thing that might take these things away from us. Iíve spent my life defending the net and I do feel that if we donít fight online crime, we are running a risk of losing it all. We have to do this globally and we have to do it right now. What we need is more global international law enforcement work to find online criminal gangs. These organized gangs that are making millions out of their attacks. Thatís much more important than you know running anti-viruses or running firewalls. What actually matters is actually finding the people behind these attacks and even more importantly, we have to find the people who are about to become part of this online world of crime, but havenít yet done it. We have to find the people with the skills but without the opportunities, and give them the opportunities to use their skills for good.
Research Note: Transcription by Diane Wiegand See Also: Vanity Fair Article on Mikko Hypponen And Also: Mikko Hypponen's Twitter Feed Animated Flag Source: http://www.crossed-flag-pins.com Page Updated: 3/27/20 Copyright Status: Text = Used with permission from the copyright owner. Image of animated flag = used with permission. Additional images (Screenshots) = Fair Use. |
|
|
© Copyright 2001-Present. |